Https Tsapps Nist Gov Publication Get Pdf Cfm Pub Id 917850
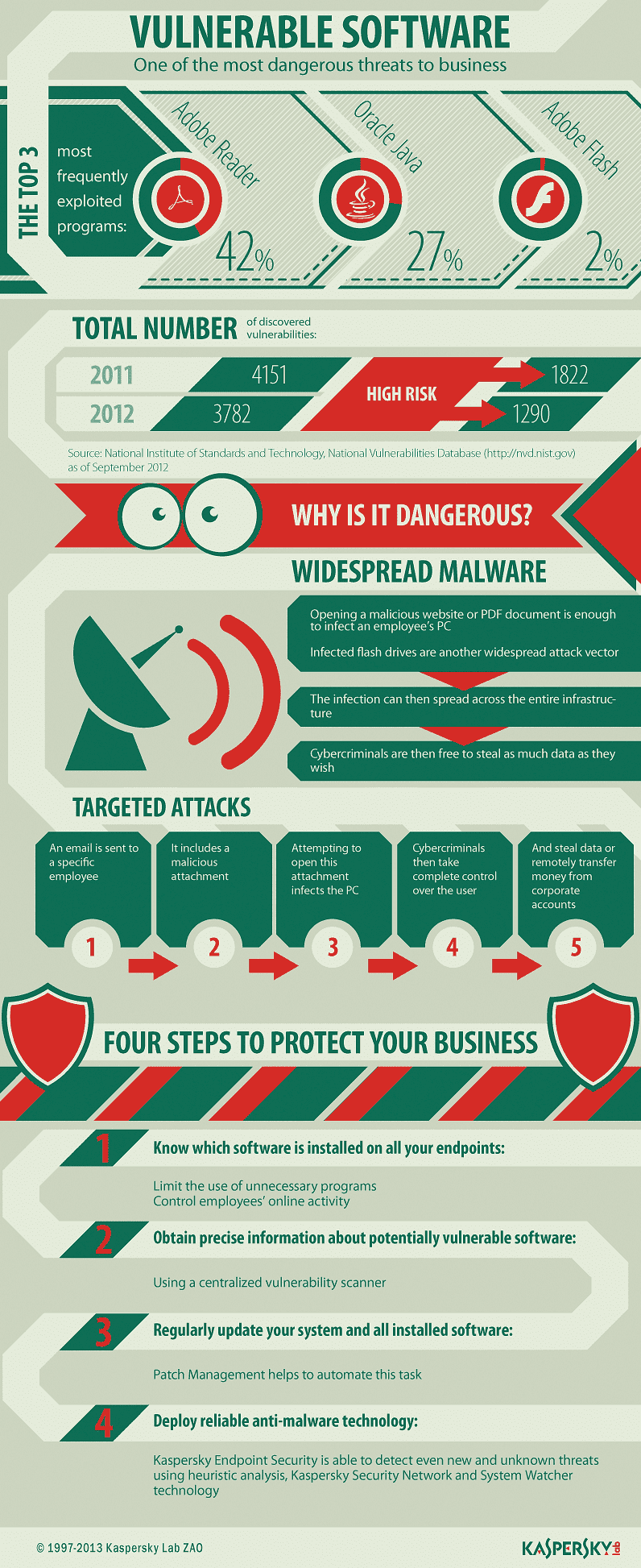
System Vulnerability Internet Security Threats Kaspersky
How Every Cyber Attack Works A Full List

Computer Exploit What Is A Zero Day Exploit Malwarebytes

What Is A Cyber Attack Recent Examples Show Disturbing Trends Cso Online

A Survey Of Emerging Threats In Cybersecurity Sciencedirect

What Is The Cyber Kill Chain And How To Use It Effectively Varonis

Spectre Security Vulnerability Wikipedia
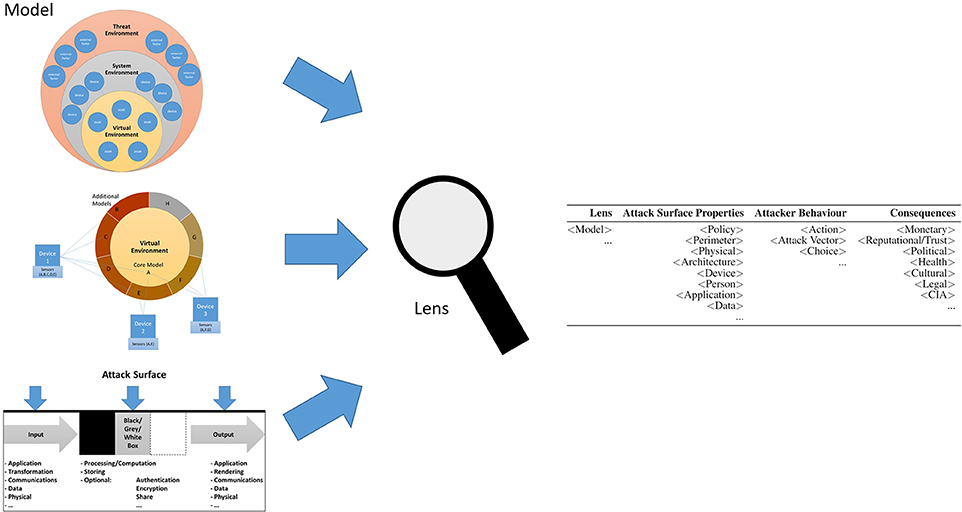
Frontiers Cyber Security Threats And Challenges In Collaborative Mixed Reality Ict

Zero Day Attacks Are Not The Same As Zero Day Vulnerabilities Fireeye Inc

What Is An Exploit

Cybersecurity High Costs For Companies

Cyber Attack What Are Common Cyberthreats Cisco

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcrwnxxtbfhcb43l925haijxrfr0 Ibw1fovtupslmv Kxcf1dra Usqp Cau

Targeted Cyber Attacks Multi Staged Attacks Driven By Exploits And Malware 9780128006047 Computer Science Books Amazon Com

Most Common Attack Vector Over Critical Infrastructures Cipsec
What Is Computer Exploit Definition From Whatis Com

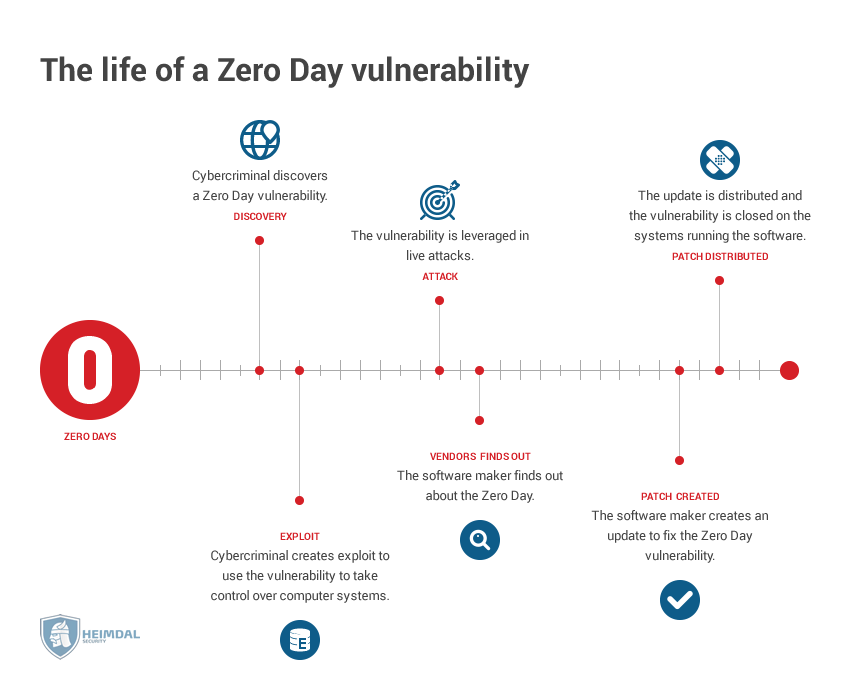
Zero Day Vulnerability Explained

What Are Exploits And Why You Should Care Malwarebytes Labs Malwarebytes Labs
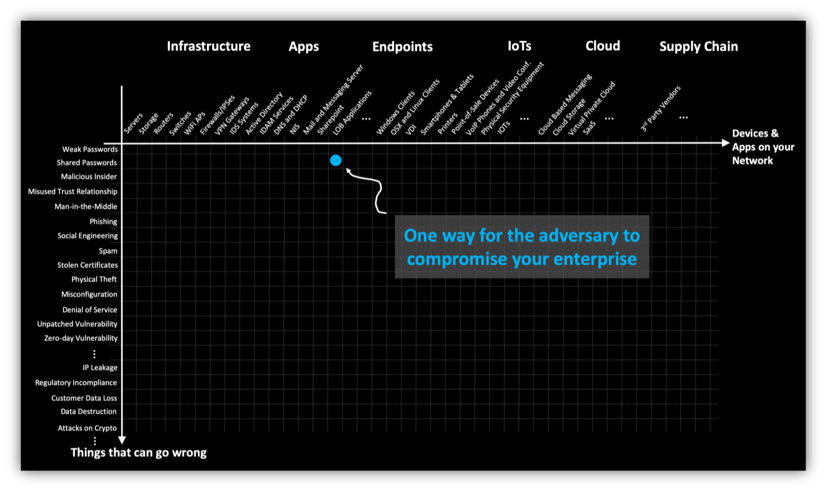
8 Common Cyber Attack Vectors And How To Avoid It Balbix

What Is A Zero Day Attack Defined Explained How It Works

Armitage Tutorial Cyber Attack Management For Metasploit
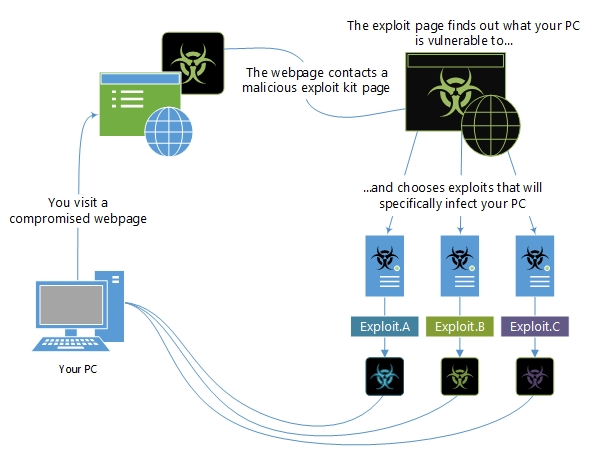
Exploits And Exploit Kits Windows Security Microsoft Docs

What Is A Threat Vector And Why Is It Important To Define Paubox

What Is Buffer Overflow Cloudflare
10 Web Security Vulnerabilities You Can Prevent Toptal

What Is Cybersecurity Introduction To Cybersecurity Edureka

Most Common Cyberattacks We Ll See In 2020 And How To Defend Against Them Zdnet
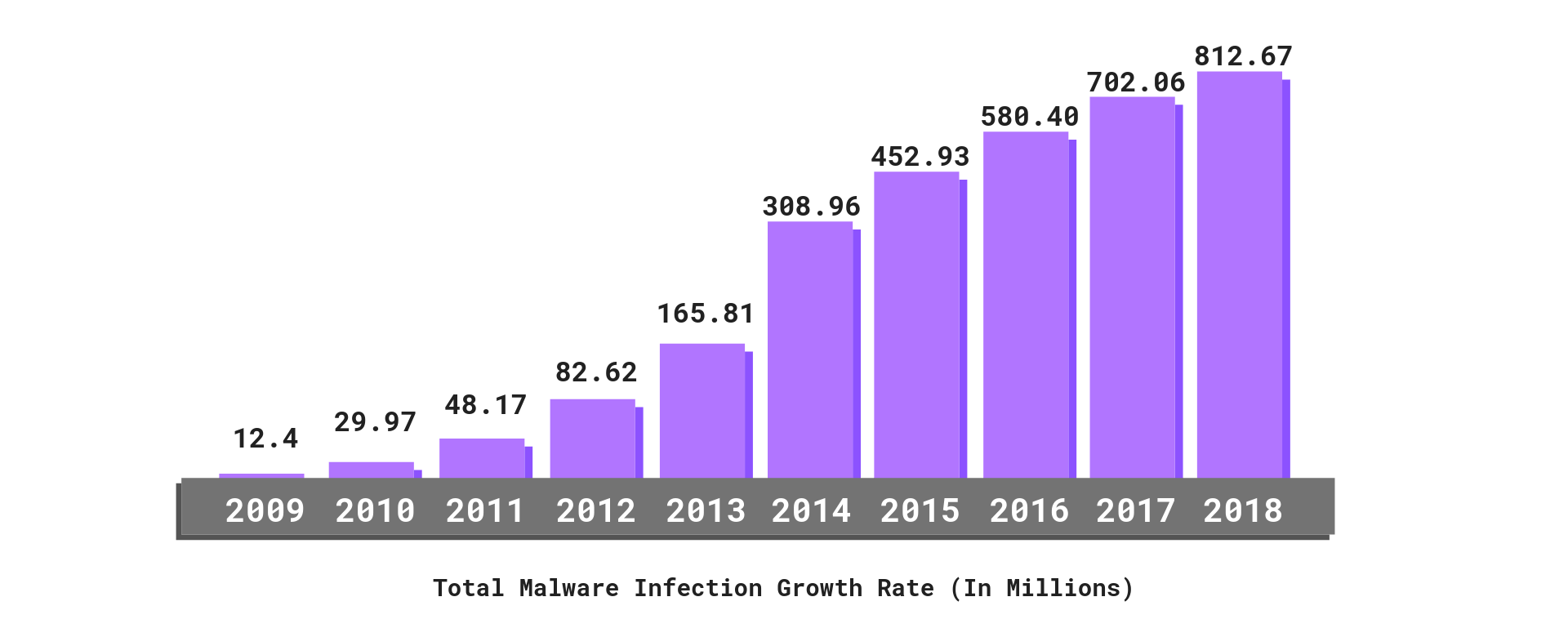
2019 Cyber Security Statistics Trends Data The Ultimate List Of Cyber Security Stats Purplesec

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcrnarhz1fiy8qmz32pvkw5jzxrwfmf Ol2zbfpsnicv4dkldpd3 Usqp Cau

What Is A Computer Exploit Exploit Definition Avast

Pre Att Ck Introduction Mitre Att Ck
Leo Understands Vulnerability Threats Feedly Blog

Ethical Issues Behind Cyber Security
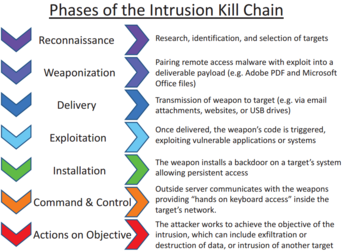
Cyberattack Wikipedia

What Is A Zero Day Attack Defined Explained How It Works
:max_bytes(150000):strip_icc()/ZeroDayExploits-584d088c714b408cbc52d958d0e03174-b090801bd1544c209bedbb3fba163ab6.jpg)
What Is Zero Day Virus Exploits Attacks And Vulnerabilities

What Is A Fileless Attack How Hackers Invade Systems Without Installing Software Cso Online

What Is Cyber Security Definition Types And User Protection Kaspersky

Threat Intelligence Definition Cyber Threat Intelligence Kaspersky

Meltdown Security Vulnerability Wikipedia

Social Engineering Explained How Criminals Exploit Human Behavior Cso Online
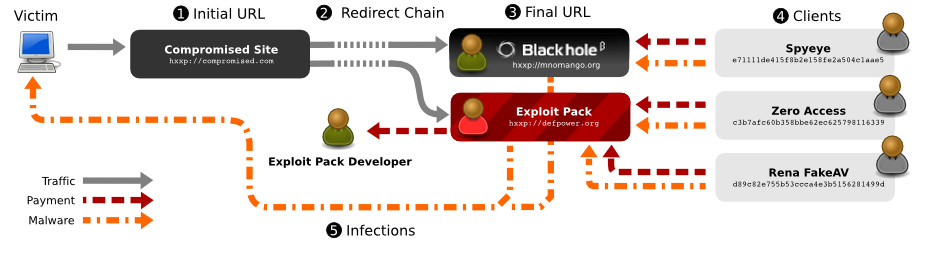
Vulnerabilities And Exploits Enisa
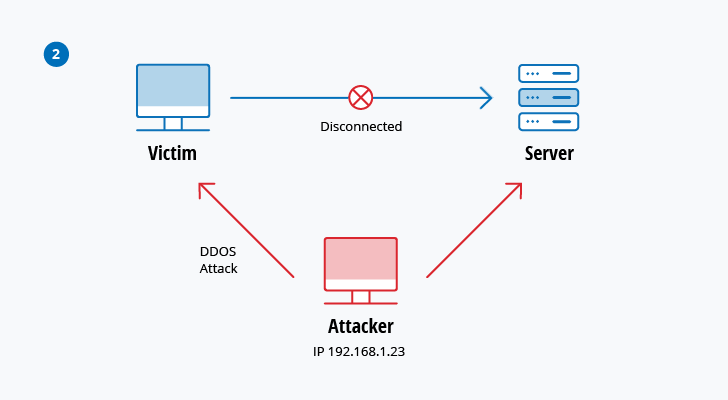
Top 10 Most Common Types Of Cyber Attacks

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqqluroxypis E26u8bhn9d5p62i9hilnkkc0w6jheqd2am 49s Usqp Cau

What Are Zero Day Attacks And How Ai Is Being Used To Combat Them Mixmode

Computer Exploit What Is A Zero Day Exploit Malwarebytes

What Is Cybersecurity Defined Explained And Explored Forcepoint

What Is Sql Injection Tutorial Examples Web Security Academy
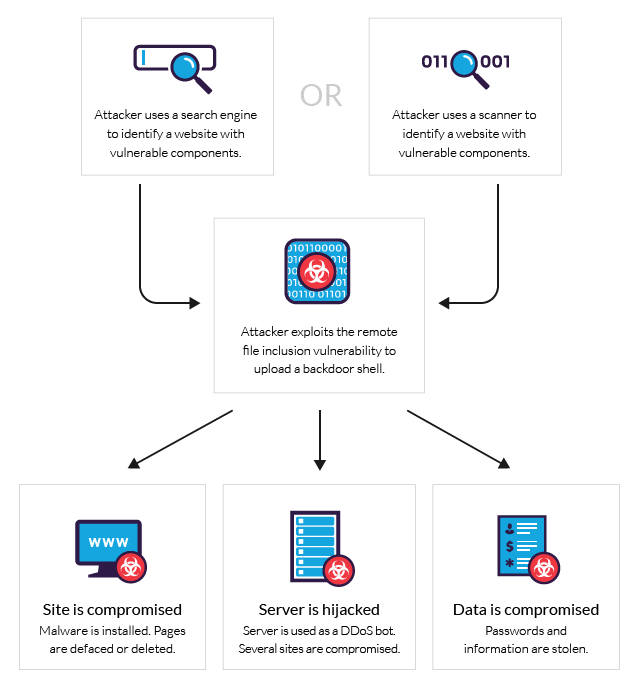
What Is Rfi Remote File Inclusion Example Mitigation Methods Imperva

How To Detect Prevent Cyberattackers From Exploiting Web Servers Via Web Shell Malware 2020 04 30 Security Magazine

Cyber Threat Basics Types Of Threats Intelligence Best Practices Secureworks
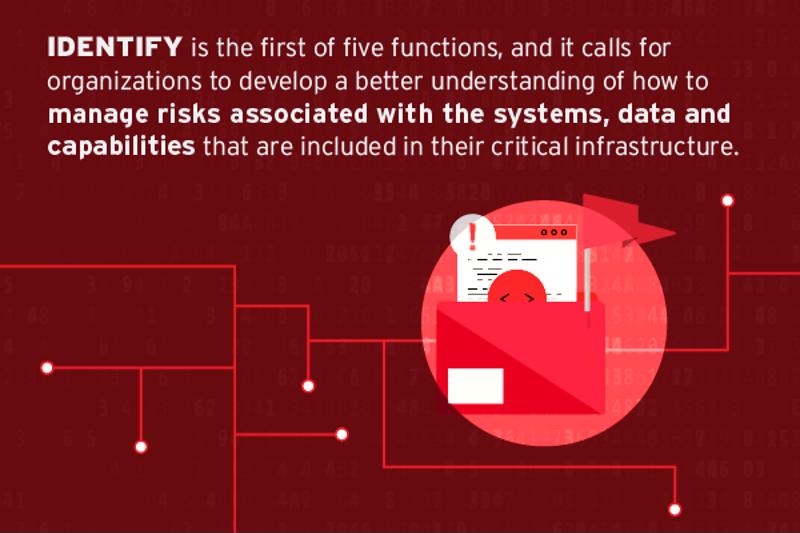
Nist Cybersecurity Framework Series Part 1 Identify

2019 Cybersecurity Almanac 100 Facts Figures Predictions And Statistics

7 Ways To Identify Darknet Cybersecurity Risks
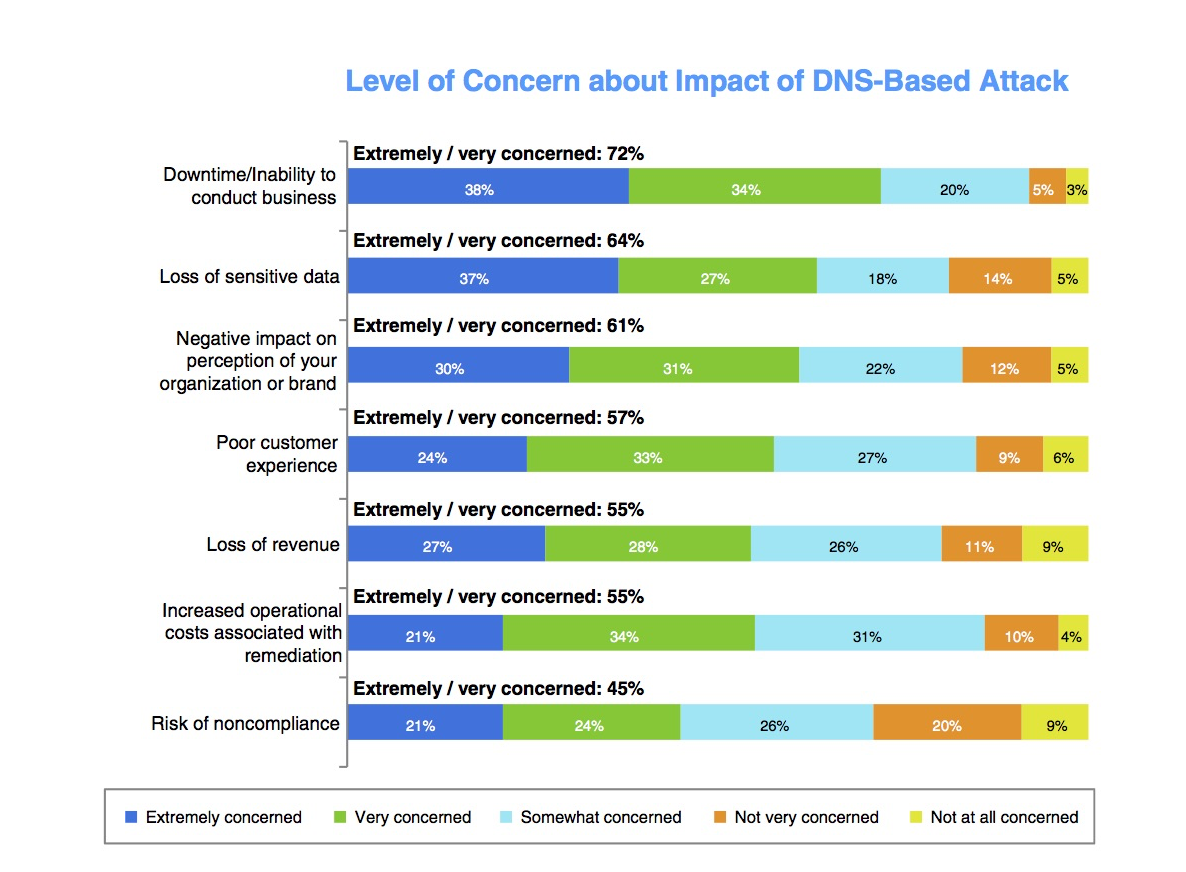
What Is A Dns Exploit Ddi Secure Dns Dhcp Ipam Infoblox
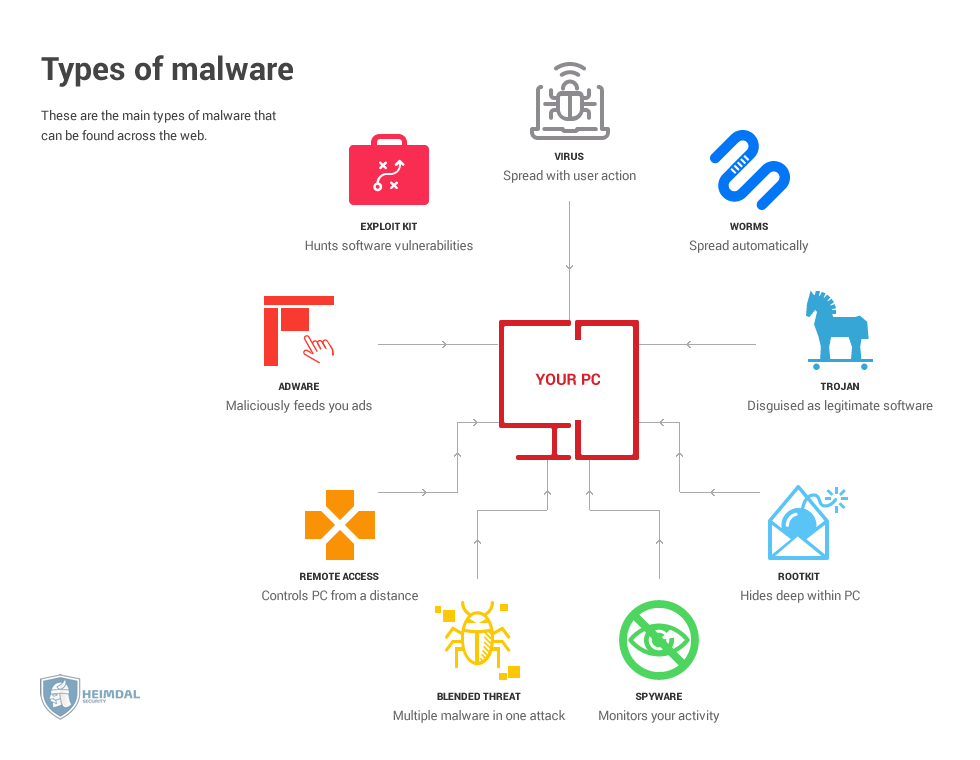
How Every Cyber Attack Works A Full List

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcryjifvpq2psgpfs4khygw16ohwazp I07rcfdub Fzxooy87mh Usqp Cau

The Top 20 Security Predictions For 2020
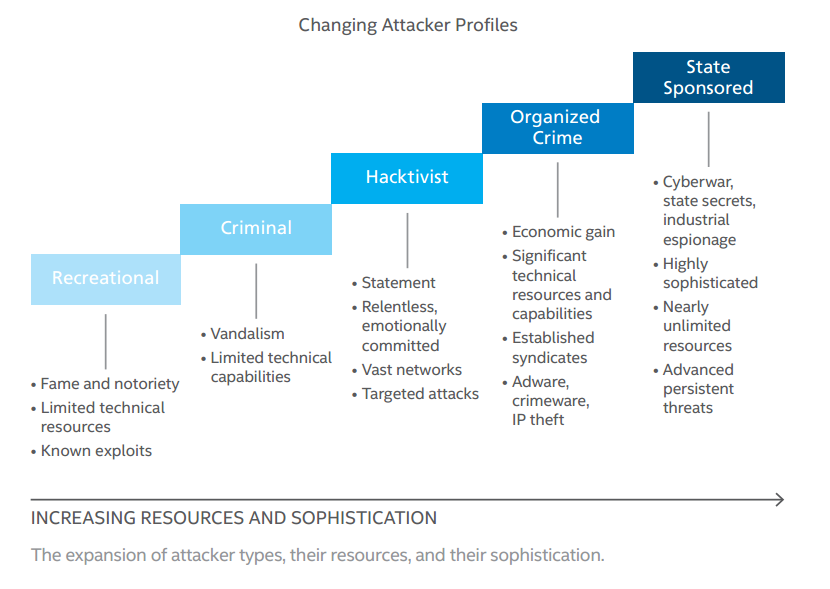
10 Alarming Cyber Security Facts That Threaten Your Data Updated
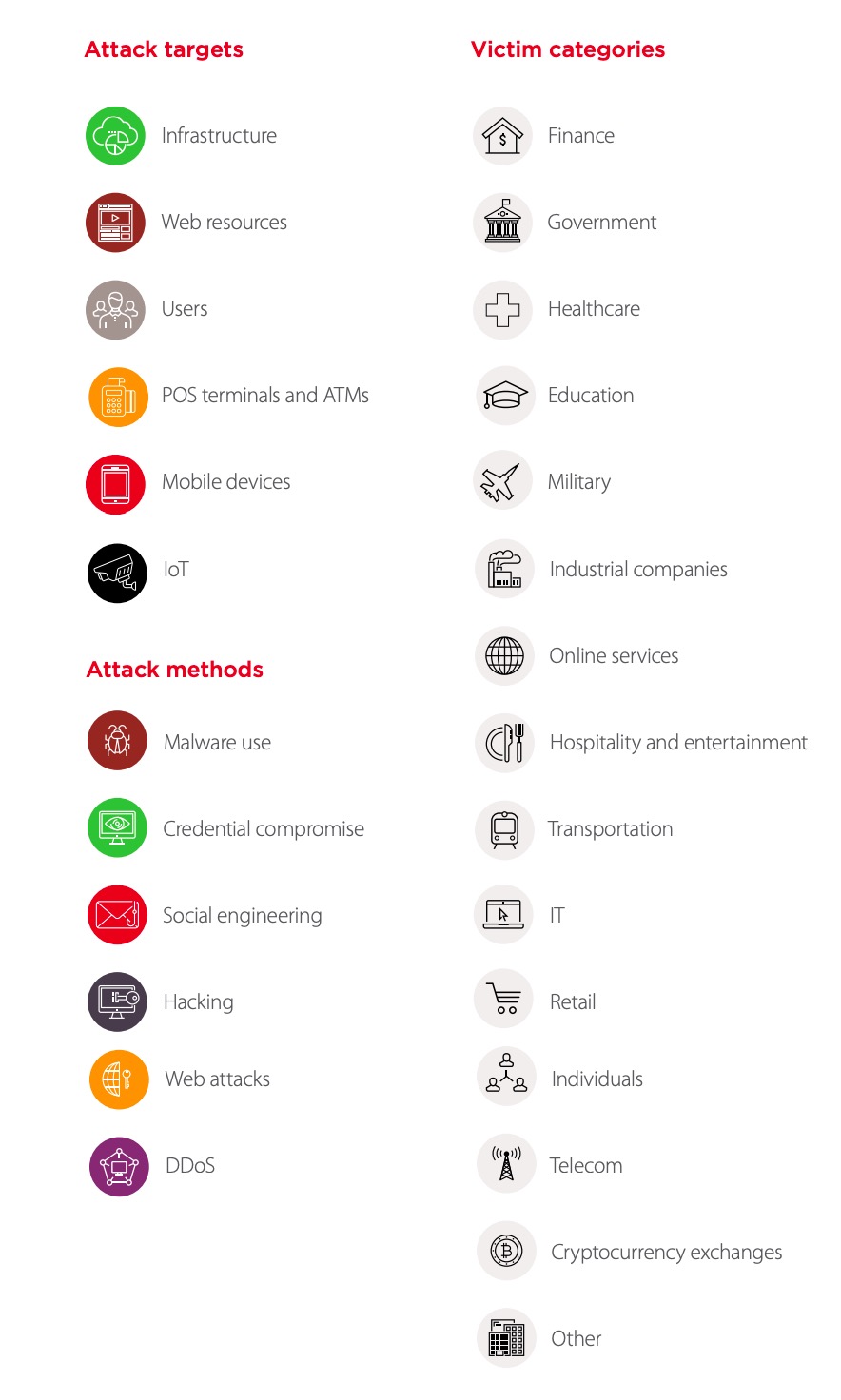
Cybersecurity Threatscape Q4 2018 Top Cyber Threats

What Are Cyber Threats And What To Do About Them The Missing Report

Threats Vulnerabilities And Exploits Oh My Icann

Risk Management Concepts And The Cissp Part 2

What Is Zero Day Exploit Definition And Risks Kaspersky

25 Cyber Security Terms That Everyone Should Know

Monitoring Ics Cyber Operation Tools And Software Exploit Modules To Anticipate Future Threats Fireeye Inc

The Top 19 Security Predictions For 2019

The Human Factor In It Security How Employees Are Making Businesses Vulnerable From Within Kaspersky Official Blog

80 Eye Opening Cyber Security Statistics For 2019 Hashed Out By The Ssl Store
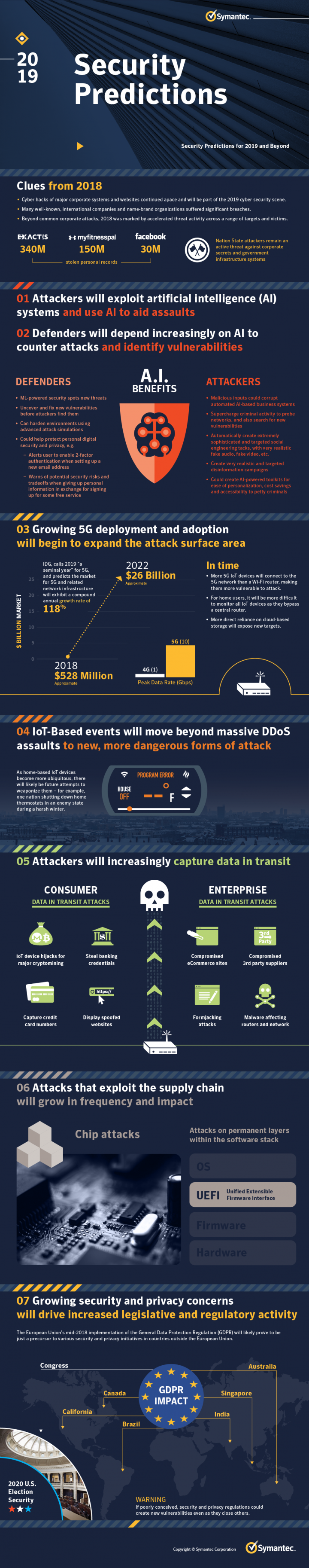
Cyber Security Predictions 2019 And Beyond Symantec Blogs
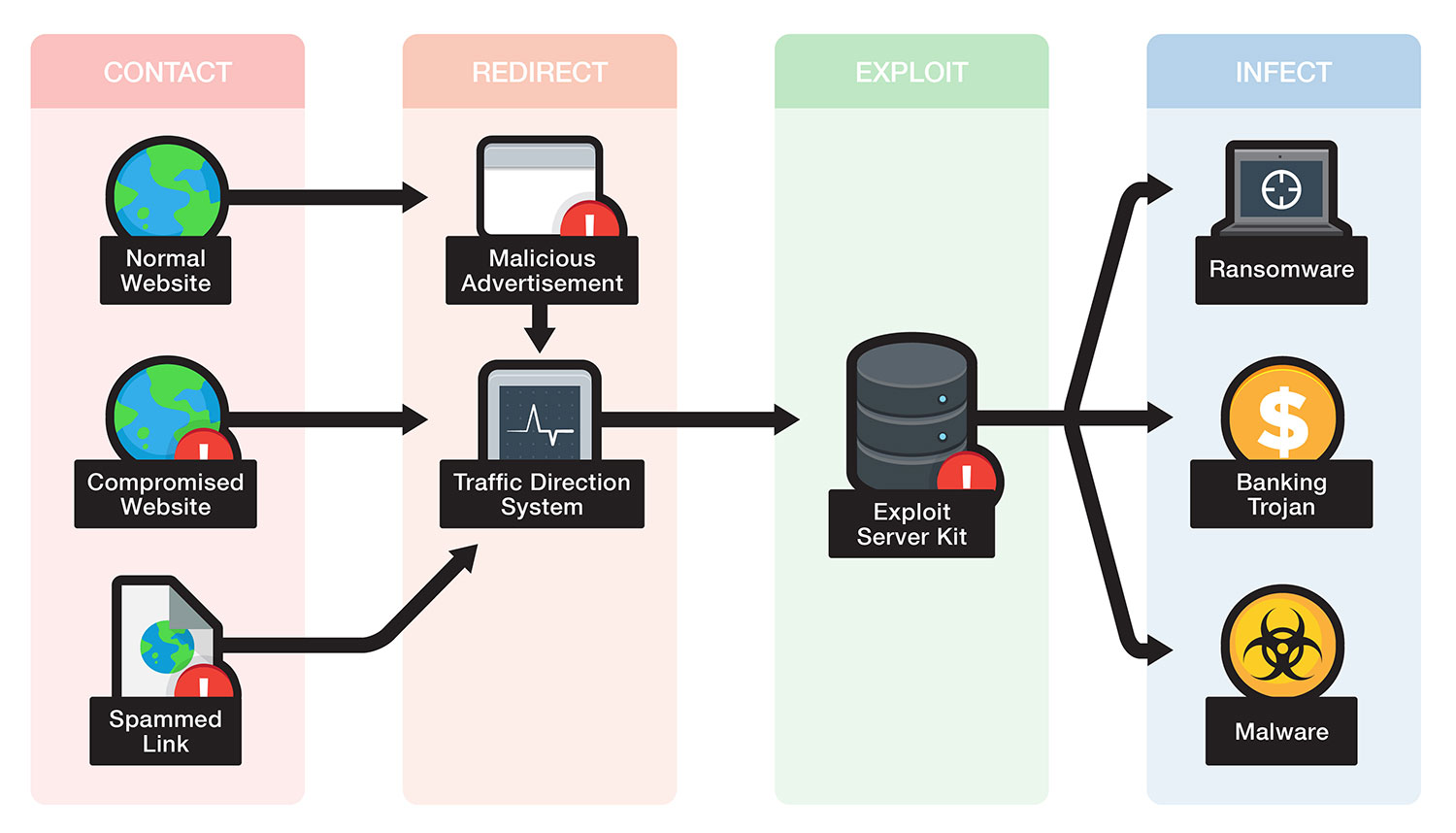
Exploit Kit Definition Trend Micro Usa
What Is An Exploit Kit With Examples How Do Cybercriminals Use Them

What Is Metasploit And How To Use This Popular Hacking Tool Cso Online

The Top 9 Cyber Security Threats That Will Ruin Your Day Hashed Out By The Ssl Store

Threat Intelligence Everything You Need To Know Recorded Future
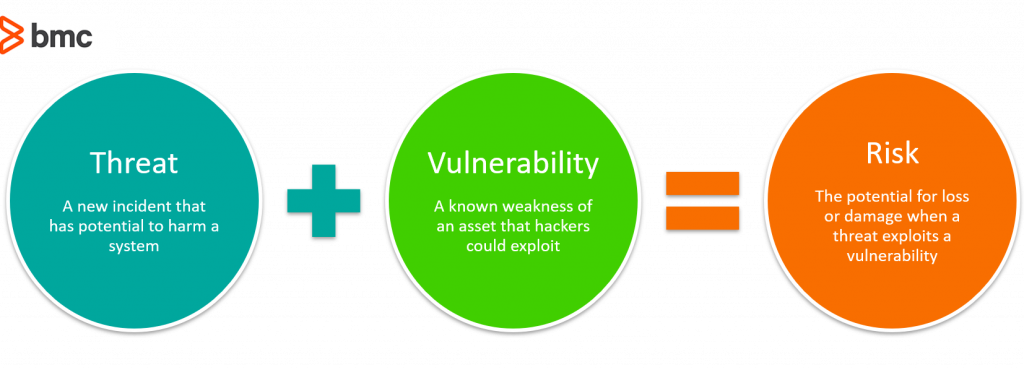
It Security Vulnerability Vs Threat Vs Risk What Are The Differences Bmc Blogs

Critical Microsoft Security Flaw Exploits Windows Handling Of Font

Cybersecurity Threat Based Defense The Mitre Corporation
Blind Regex Injection Theoretical Exploit Offers New Means Of Forcing Web Apps To Spill Secrets The Daily Swig

Cybersecurity And Digital Trade Getting It Right

Https Securitylab Disi Unitn It Lib Exe Fetch Php Media Teaching Seceng 2016 Cybrisk 2016 08 Threats Vulns Exploits Pdf
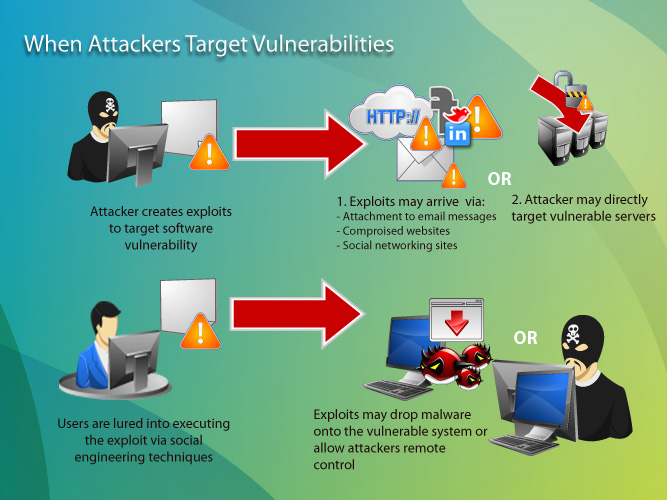
Exploit Definition Trend Micro Usa
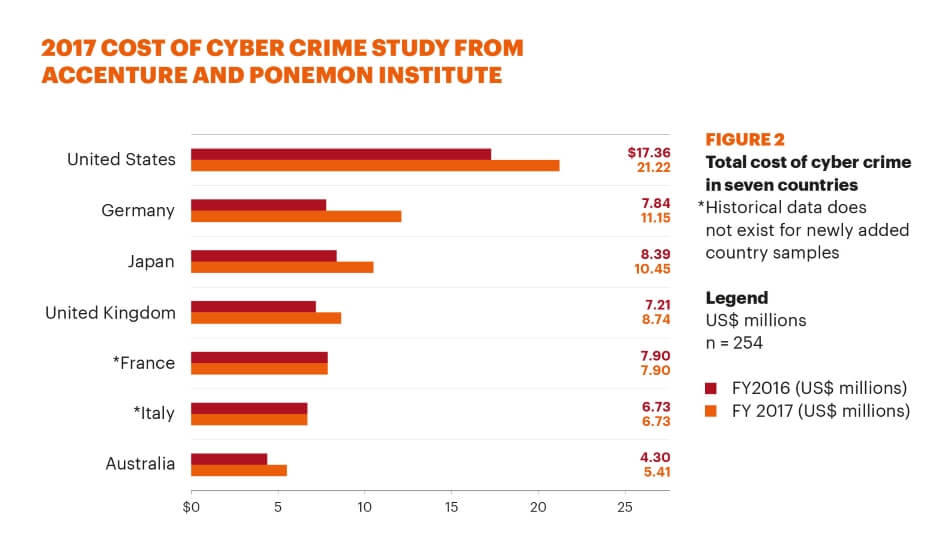
10 Alarming Cyber Security Facts That Threaten Your Data Updated

What Are The Most Common Cyber Attack It Governance Usa
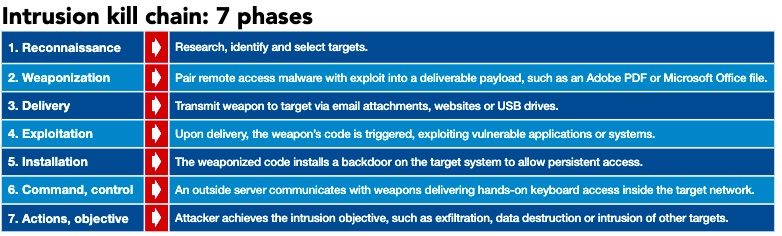
Control Engineering Understand The Cyber Attack Lifecycle

2
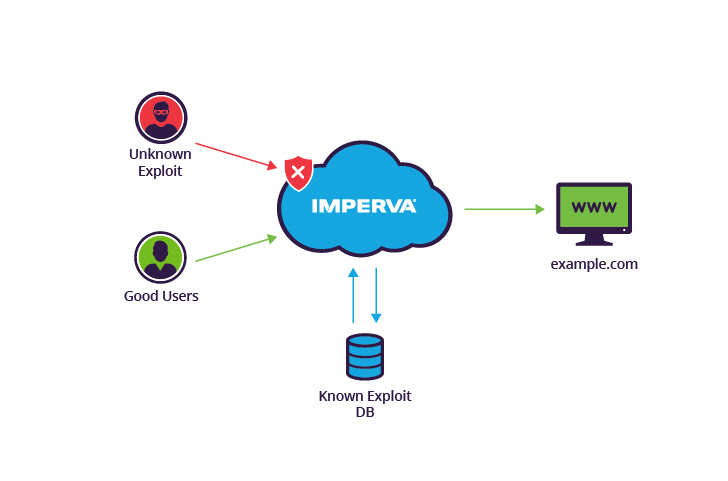
What Is A Zero Day Exploit Protecting Against 0day Vulnerabilities Imperva

What Is Privilege Escalation And Why Is It Important Netsparker

Public Sap Exploits Could Enable Attacks Against Thousands Of Companies Cso Online

The Approach To Risk Based Cybersecurity Mckinsey
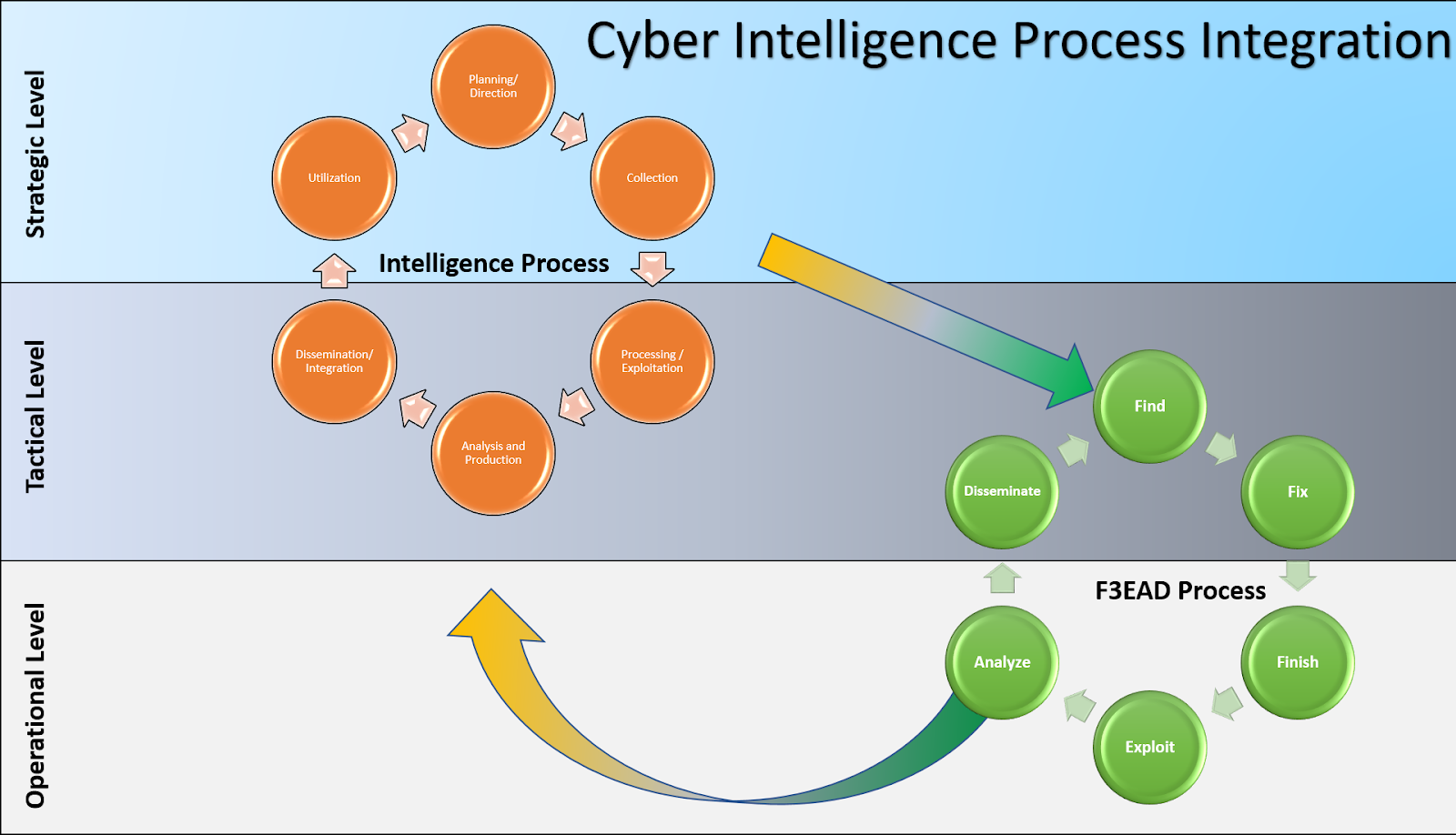
Methods And Methodology Cyber Threat Intelligence Sig Curriculum

Cybersecurity 101 Intro To The Top 10 Common Types Of Cyber Security Attacks Infocyte

Network Security Malicious Threats And Common Computer Definitions
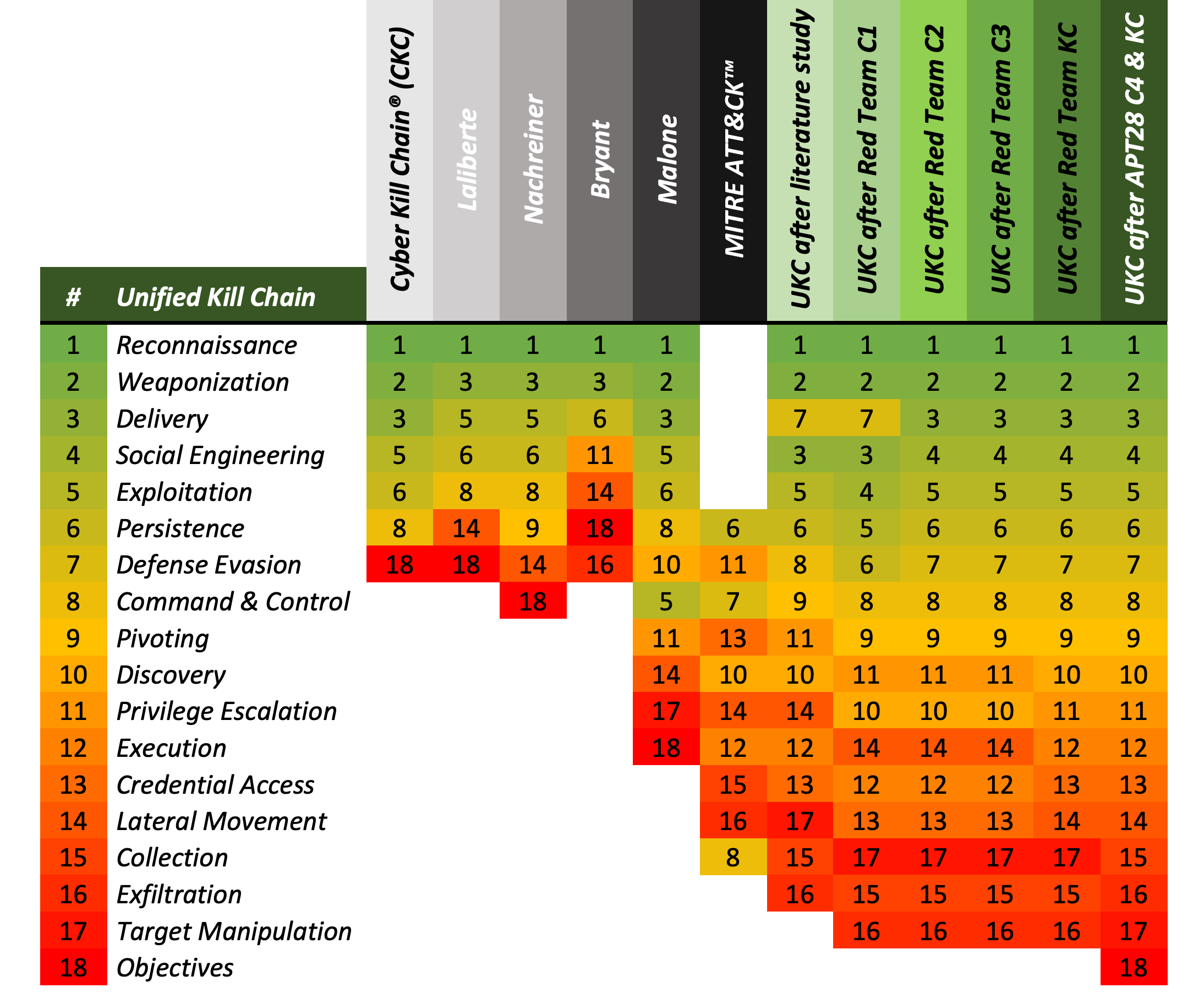
At The Core Of Cybersecurity Are Risks Costs Benefits And Threat Models By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium
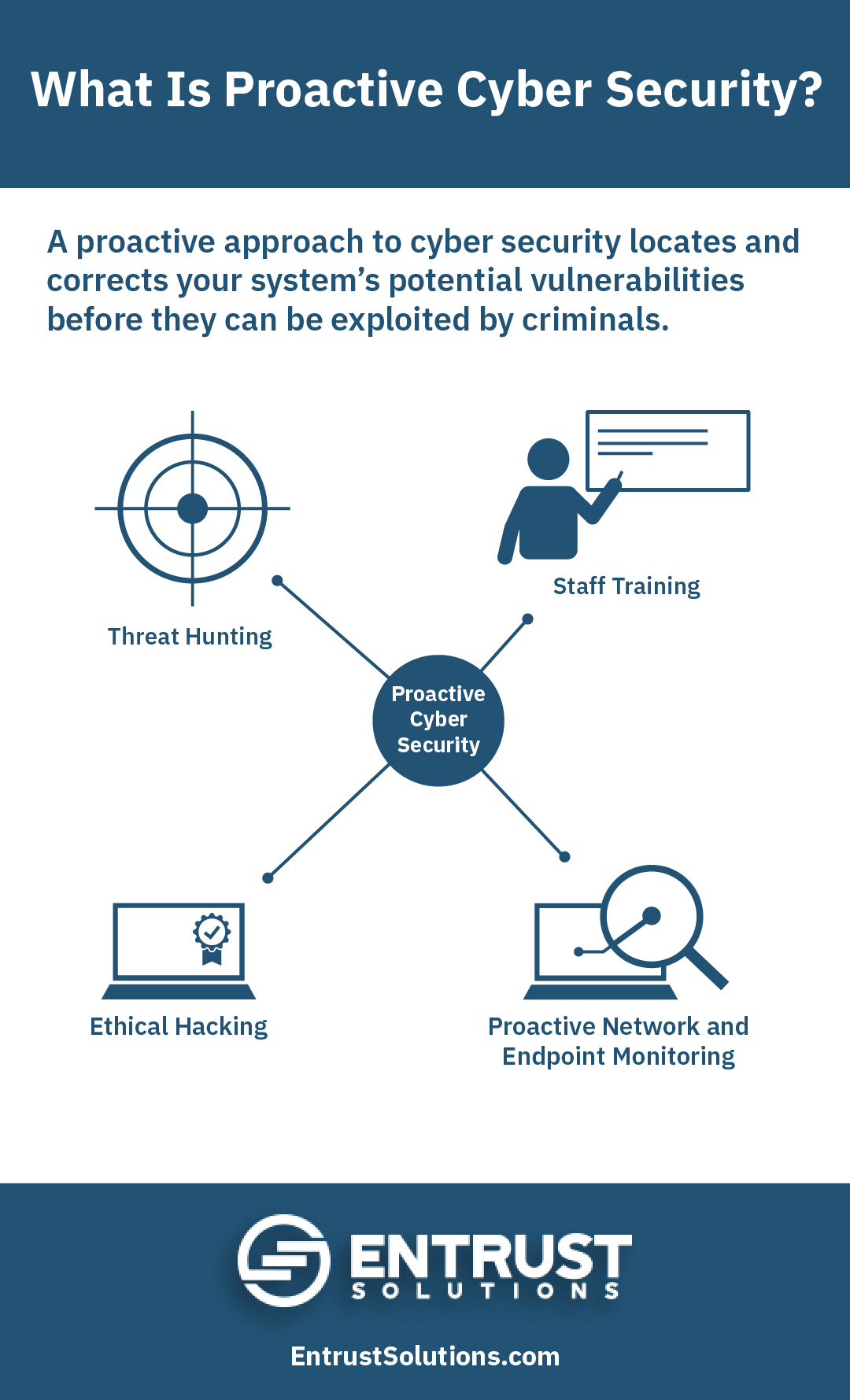
Proactive Vs Reactive Cyber Security For Your Business Entrust Solutions






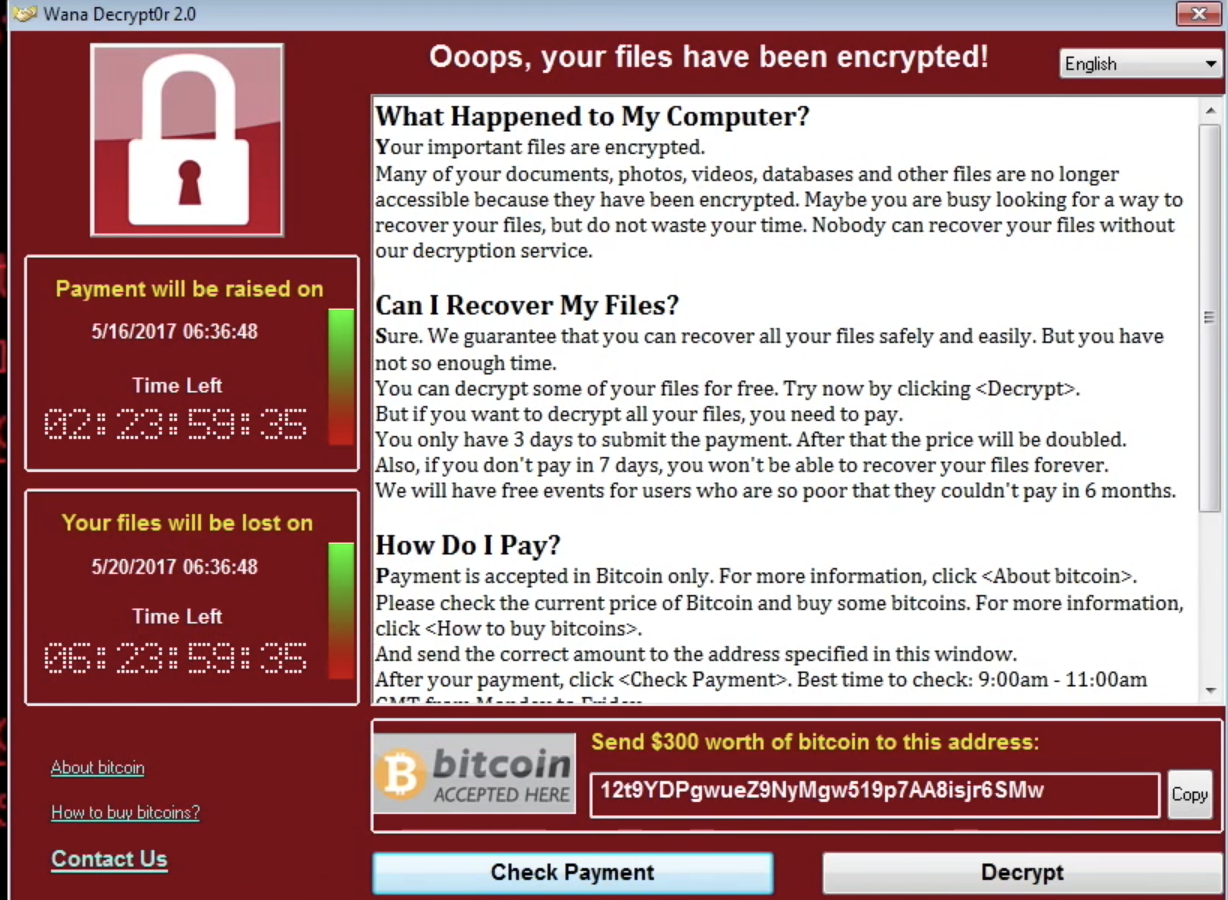

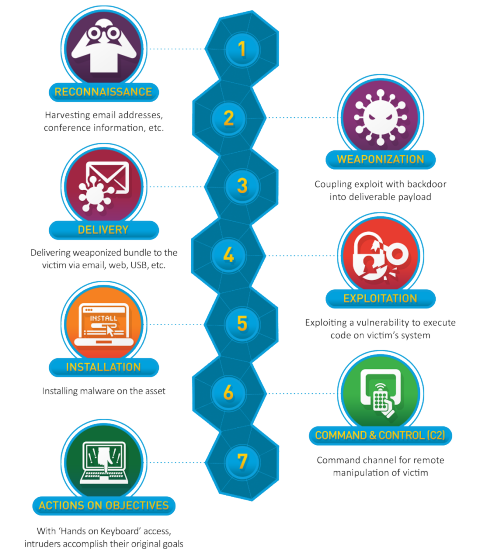





































:max_bytes(150000):strip_icc()/ZeroDayExploits-584d088c714b408cbc52d958d0e03174-b090801bd1544c209bedbb3fba163ab6.jpg)